Bookmarks of the Year 2007
- Here is the Complete bookmark of this years articles published on this site (http://bcdalai.blogspot.com/). Please go through to find out all the popular article here.
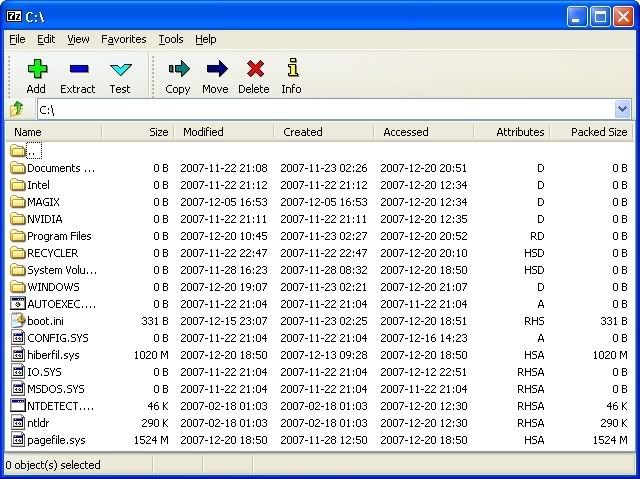
- Complete Review of 7-Zip-Best Compression Tool
- 7-Zip is a file archiver with the high compression ratio. The program supports 7z, ZIP, CAB, RAR, ARJ, LZH, CHM, GZIP, BZIP2, Z, TAR, CPIO, RPM and DEB formats. Compression ratio in the new 7z format is 30-50% better than ratio in ZIP format.
- Microsoft Office 2007 Service Pack 1 delivers stability and performance improvements
- The 2007 Microsoft Office suite Service Pack 1 delivers important customer-requested stability and performance improvements, while incorporating further enhancements to user security. This service pack also includes all of the office updates.
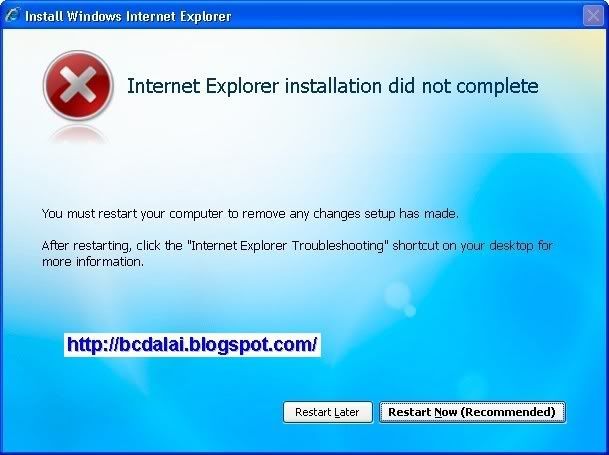
- Unable to Install Internet Explorer 7 on Windows error message
- If you are trying to install the IE7 on Windows XP with Service Pack 2 or Service Pack 3 RC or in other versions of Windows. In the installation process you will see that it passes the WGA check, but the installation fails at the end and the error message
- The "Microsoft" name is being auctioned for no less than $1 million on eBay
- The other is a Portuguese company that registered its name back in 1981. Of course, it is a coincidence, rather than a case of stolen identity.
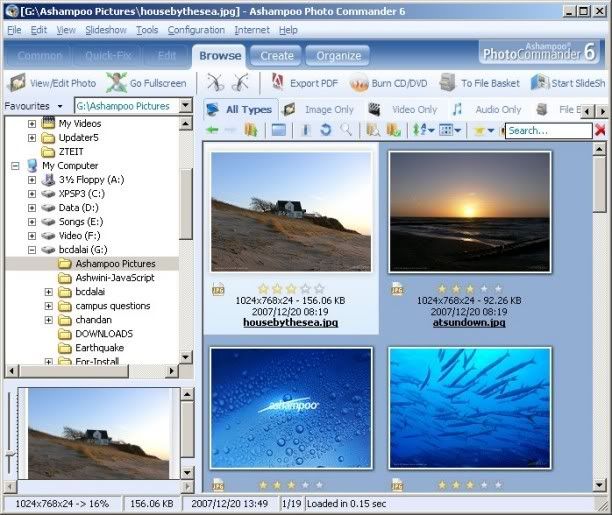
- Complete Review of Ashampoo Photo Commander. All-in-one application for managing your photo collections.
- Ashampoo Photo Commander 5 is an all-in-one application for organizing, editing, sharing and presenting photo collections. It also features additional creativity tools and audio and video management capabilities, making it a complete media management pack
- Inside Windows Vista SP1. Windows Vista Service Pack 1 RC.
- Windows Vista Service Pack 1 RC includes all previously released updates for the operating system. This update also includes a small number of new functionalities, and many updates, which change significantly change customers’ experience with the operat
- Complete review of this Windows XP SP3. Download Windows XP SP3 RC1.
- Windows XP Service Pack 3 (SP3) includes all previously released updates for the operating system. This update also includes a small number of new functionalities, and many updates, which change significantly change customers’ experience with the operat
- Known/Unknown Facts on Windows
- Here are some common facts about Windows and Microsoft software product and technology.
- Windows Server 2008 Line-up and Pricing
- Like Windows Vista, Windows Server 2008 will be available in a multitude of product versions; eight to be precise, three of which include Hyper-V: Windows Server 2008 Standard, Windows Server 2008 Enterprise and Windows Server 2008 Datacenter.
- 100 Favorite Blogs of 2007
- This article contains the names of all those blogs that are the favorite in the year 2007. These are the 100 favorite blogs of the year 2007, which was first discovered and fully reviewed by PC Magazine. This list contains various types of favorite blogs
- Security Glossary
- Security Risks: Adware Backdoor Botnet Crimeware Dialers Downloader Hack tools (keygens/cracks/patches) Joke programs Keylogger / Keystroke Recorder Macrovirus Malbot Mass Mailer Pop-ups Pornware Remote Access Riskware Rootkit Spyware T
- Restore your PC settings after cleaning viruses, spywares
- Security is the most important concept in computing. So everyone needs to be secure to make the data and application to avoid loss. The object of this article is to give some awareness to the computer users to protect the data, time and money. If you have
- TuneUp Utilities 2008 is released !!!
- The new version of TuneUp Utilities i.e. version 2008 is now ready to arise and the countdown has started. After a few more days “TuneUp Utilities 2008” will be released!
- Ashampoo Burning Studio 7
- Ashampoo Burning Studio 7 keeps the power and simplicity that made version 6 such a runaway success and adds several major new functions, including DVD video burning, modified copies and bootable discs. These are all functions that users of previous versi
- World’s 4th fastest supercomputer from India
- India has ranked into the Top Ten in list of the fastest supercomputers in the world, becoming a global IT power.A cluster platform at Pune's Computational Research Laboratories (CRL), a Tata subsidiary, has been ranked fourth in the widely anticipated To
- The new release of RealPlayer 11 Build 6.0.14.738
- The new version of RealPlayer is the all-in-one digital media player that lets you find anything and play everything. The new RealPlayer gives you the ability to download them all to your personal video playlist. Grab videos from thousands of Web sites with realplayer
- All 35 official Windows Vista Ultimate MUI Packs (x86 & x64)
- Here are all ever published official 35 Multi-Language Packs for Microsoft Vista Ultimate users. Direct download links fresh from the Microsoft Windows Update-server!
- Control users’ temporary Internet files and browser history using Windows Server 2003 Group Policy
- Control users’ temporary Internet files and browser history using Windows Server 2003 Group Policy
- Software Problems Solutions Comments-bcdalai
- Ask Your Questions Here. Question on software problems.
- All About Windows XP Service Pack 3
- New features in Windows XP Service Pack 3. all informations about Windows XP Service Pack 3.
- Administrative Power Tricks
- Commands and tips for administrator windows user for troubleshooting everyday computing issues.
- Integrate service packs into Windows and Office
- Integrating service packs into the windows or office installations make it easier for administrator to deploy and manage. It saves both time and costs for the enterprise to apply the service pack updates.
- 1000+ Run Commands in "Windows Command Guide 2007"
- More than 450+ Run commands and over 1000+ of command tips for everyday use and for administrator. This guide will help you speed up your administrative capability by using commands.
- 140+ Microsoft Secret Codenames Released
- Describes the codenames of different Microsoft software and technology. This document describes the codenames, name of the product and descriptions.
- Complete Vista folder and file informations
- Vista Folder-File Info. describes each and every system folders and some important file names. It describes the uses of the folder and describes why it in the Windows Vista OS.
- New software downloads-bcdalai
- New Software Downloads Oct 2007. Direct download links to new release softwares. Most favorite softwares and best softwares.
- Babylon 7.0 the powerful dictionary - A Review
- Babylon is a powerful dictionary, translation and Currency conversion software
- Complete Hardware Glossary for IT Pro
- Hardware Glossary for IT Professional
- Technology News-01
- Microsoft Windows News
- 1000+ Tech. Acronyms
- 1000+ TECH. ACRONYMS
- Recommended Daily Used Softwares
- Common used program and links for everyone
- Microsoft Windows Operating System Release Dates
- Microsoft Windows OS Release Dates
Posted by: bcdalai